IPSec VPN (Inseego Connect)
You can create IPSec VPNs using Inseego Connect. To learn more about the benefits of Inseego Connect, go to https://inseego.com/products/cloud-management/inseego-connect/. You can sign up for a free Inseego Connect account at connect.inseego.com.
NOTE: This feature may not be available, depending on your service provider.
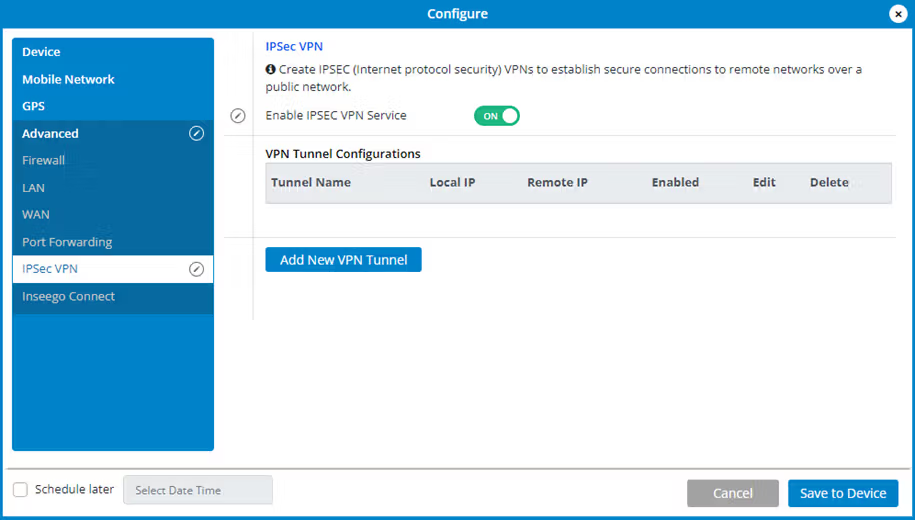
Move the Enable IPSEC VPN Service slider to ON to enable IPSec VPN service.
When IPSec VPN service is enabled, established tunnel information displays. You edit or delete existing tunnels.
Click Add New VPN Tunnel to add a new VPN tunnel. The Add New VPN Tunnel Dialog appears.
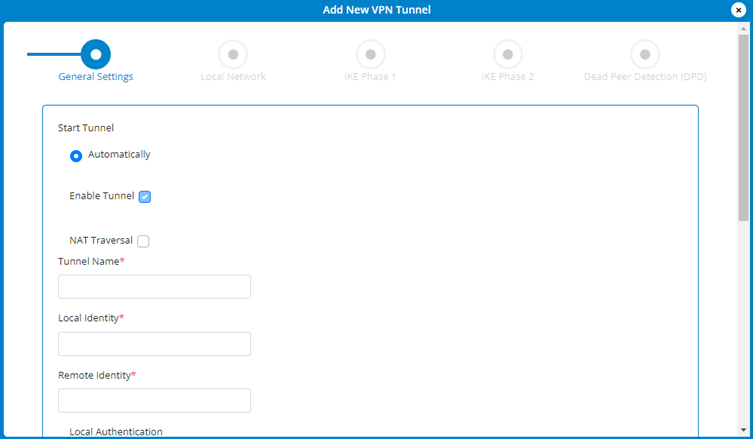
General Settings
- Start Tunnel — Select whether to start the tunnel automatically upon start up or manually.
- Enable Tunnel — Check this box to enable the tunnel.
- NAT Traversal — Check this box if you want NAT traversal to automatically detect if network address translation (NAT) is being performed between the two VPN tunnel endpoints.
- Tunnel Name — Enter a unique name to identify this VPN.
- Local Identity — Enter a unique name to identify the local point of the tunnel.
- Remote Identity — Enter a unique name to identify the remote point of the tunnel.
- Local Authentication — Select a type of authentication from the drop-down list. You are prompted for further information based on your selection.
- Remote Authentication — Select a type of authentication from the drop-down list. You are prompted for further information based on your selection.
Click Next.
Local Network
- Local IP — Enter the WAN IP address of local device. NOTE:This should be a static IP that you are able to reach from remote device (no NAT).
- Local Subnet Mask — Enter the subnet mask of the local device, for example: If your local IP is 192.168.0.100 and your subnet mask is 255.255.255.0 this should be 192.168.0.0/24. NOTE: This should mirror what the subnet displays in the local device, for example: 192.168.0.0 / 255.255.255.0. NOTE: The local device should be on a different subnet from remote, for example: If the Remote Subnet Mask is 192.168.1.0/24, the Local Subnet Mask might be 192.168.0.0/24. This is usually based off the DHCP settings of the devices.
Remote Network
- Remote IP — Enter the WAN IP address of remote device. NOTE: This should be a static IP that you are able to reach from a local device (no NAT).
- Remote Subnet Mask — Enter the subnet mask of the remote device, for example: If your remote IP is 192.168.1.100 and your subnet mask is 255.255.255.0 this should be 192.168.1.0/24. NOTE: This should mirror what the subnet displays in the local device, for example: 192.168.1.0 / 255.255.255.0. NOTE: The remote device should be on a different subnet from local, for example: If the Local Subnet Mask is 192.168.0.0/24, the Remote Subnet Mask might be 192.168.1.0/24. This is usually based off the DHCP settings of the devices.
Click Next.
IKE Phase 1
Key Lifetime: The lifetime of the phase 1 key, in seconds.
Select desired items from each column. NOTE: Each phase should support at least one matching option in each column. For example, if Phase 1 on this page is configured to support Hash SHA2 512, SHA2 384, and SHA2 256, then at least one of those selections must be selected in Phase 2 on the next page in order to be a common Hash.
Click Next.
IKE Phase 2
Key Lifetime: The lifetime of the phase 2 key, in seconds.
Select desired items from each column. NOTE:Each phase should support at least one matching option in each column. For example, if Phase 1 on the previous page is configured to support Hash SHA2 512, SHA2 384, and SHA2 256, then at least one of those selections must be selected on this page to be a common Hash.
Click Next.
Dead Peer Detection (DPD)
Dead Peer Detection (DPD) is a keep-alive method that ensures the tunnel is up and will take action if it is not able to reach the remote side of the tunnel, depending on what DPD action you select. You can use the default values, if desired.
- Enable: Check this box to enable DPD.
- DPD Action: Use the drop-down to select a DPD action.
- DPD Delay: The number of seconds between DPD packets.
- DPD Timeout: The number of seconds the router will allow an IPSec session to be idle before beginning to send DPD packets to the peer machine.
Click Next and implement your settings. The new VPN tunnel is displayed on the IPSec VPN page.
